Note
All In: US Places a Big Bet with October 17 Controls
US policymakers are wagering that industry and partners will align with US controls and that time and innovation are on Washington's side.
New US tech controls will force a mindset shift for a wide range of industries on how their products could be national security risks.
The US has launched its next wave of tech controls, this time with a focus on the cross-section of data security and cybersecurity concerns around China. The US administration asserts that its proposed rules on human personal data and connected vehicles are narrow and targeted, but there are no small yards in regulating the digital economy. Internet of Things ecosystems rely on the interconnectivity of devices, people, and data flows, making virtually every node a potential risk vector. With the new US moves affecting a wide range of industries, from connected vehicles to biotech, companies will need to undergo a mindset shift toward more proactively assessing how their products, services, and data flows could pose national security risks to US critical infrastructure and US persons, and what mitigation measures to take—to include potentially unwinding relationships with Chinese partners and suppliers.
The Biden administration made two big back-to-back announcements last week—a much-anticipated executive order and accompanying Advance Notice for Proposed Rulemaking (ANPRM) on data security—alongside a Commerce ICTS investigation into connected vehicles. The data security executive order focuses on personal data genomic data, biometric data, personal health data, geolocation data, financial data, and certain kinds of personal identifiers. The ICTS investigation by Commerce focuses on transactions relating to the ICT supply chain for connected vehicles.
Under the Sullivan doctrine, US tech controls aimed at China began with the most tangible target: advanced semiconductors and the tools used to make them. They soon expanded to cover the intangibles: restrictions on US outbound capital and know-how to Chinese firms in a “small yard” of force-multiplying technologies—semiconductors, AI, and quantum computing, but not (yet) biotech. Then came novel Infrastructure-as-a-Service measures for cloud service providers to monitor and restrict access to high-performance compute capacity, a work in progress that aims in part to prevent Chinese entities from using the data centers utilizing high-end chips to conduct training runs for large AI models.
In this next wave, US tech controls are permeating a broader domain, covering the data flows and ICT conduits that power an increasingly digitalized economy. As a result, the implications will be far-reaching for a range of industries, challenging the notion that US tech ring-fencing can be confined to a small yard.
The data security and cybersecurity measures work in tandem. If the theory of harm is that US sensitive data can be collected and exploited by bad actors, then step one is to shore up definitions on what constitutes sensitive data, step two is to identify all the ways—both licit and illicit—that data can be transmitted to those bad actors, and step three is to scrutinize the technology itself that enables the collection, storage, and transfer of data in connected systems, which in turn could create backdoors for malicious cyber behavior.
On paper, the data security EO and associated ANPRM are relatively narrow in scope and intent. They plug holes in the US’s patchwork approach to data security rules but stop short of establishing a full-blown data security regime like the EU’s GDPR.
Prohibitions focus on the transfer of Americans’ bulk personal data, genomic data, and US government-related data to countries of concern. In justifying restrictions, the policy documents outline a theory of harm on how such data can be used for malicious intent: health and financial data that reveal vulnerabilities along with data on daily routines, habits, and patterns of individuals may be harnessed to spy, blackmail, coerce, influence, or intimidate US persons. The DOJ is tasked with establishing a licensing process and risk-based compliance program for companies to adopt and mitigate access to data by countries of concern (see Table 1).
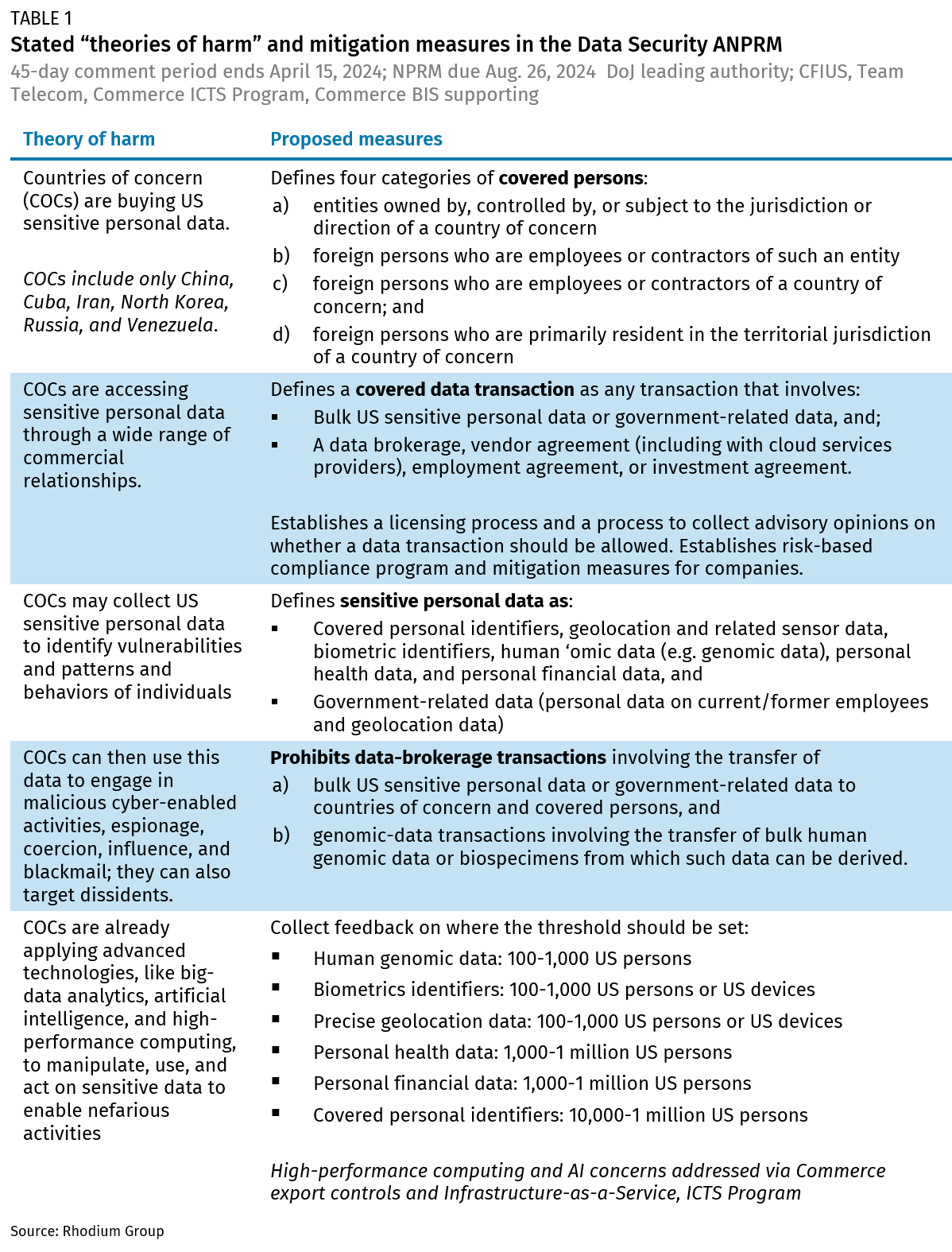
Despite its apparent narrow scope, the impact of the data security measures could end up being quite broad. In fact, in one fell swoop, the Biden administration appears to be addressing several long-standing policy debates. For example:
The data security measures should be seen as a building block toward a more cohesive data security regime. For now, the US has kept the focus on sensitive personal data on US persons. But as AI models accelerate the expansion of data banks and as infrastructure becomes more interconnected in a fast-growing digital economy, other non-human and non-personal data could eventually be considered sensitive from a national security perspective (e.g. genetic sequences of crops or livestock, or data tied to the operationality of US critical infrastructure, including transportation, telecom, energy, water, and financial services).
At this stage, the US may be reticent to go beyond personal data in classifying other types of sensitive data subject to restrictions under this framework. Indeed, the latest data security measures discuss at length how the US is committed to a free and open internet and is not sliding toward a more state-heavy, generalized data security regime with, for example, broad restrictions on cross-border data flows and requirements on data localization.
But other tools are in development to address growing data security concerns around non-personal but still highly sensitive data. For example, government-funded research can be subject to tighter oversight and limited access to countries of concern. The US is still in the early stages of establishing oversight of foundational AI models and underlying training data, with a recent Executive Order on Artificial Intelligence that requires government agencies to designate Chief AI Officers and coordinate with the National Institute of Standards and Technology (NIST) under Commerce in advancing a framework for assessing AI-related risks. Moreover, Commerce export controls are expanding to cover Infrastructure-as-a-Service, placing a growing burden on cloud service providers to monitor for potentially harmful end-use. Export controls may further evolve to cover certain classes of important data as IP.
The US can also target the ICT conduits that facilitate data flows more broadly. The US has expansive authorities to deny market access to companies of countries of concern that supply internet equipment and software, from Wi-Fi modules and base stations to software stacks and cloud services to the sensors and chips that power these systems. This is where the US commitment to a free and open internet and cross-border data flows contains an important qualifier: the free flow of data across borders must be facilitated by secure and trustworthy ICT infrastructure.
To that end, the data security measures task the DOJ-led Committee for the Assessment of Foreign Participation in the US Telecommunications Services Sector (also known as Team Telecom) to prioritize reviews of submarine cable system licenses linked to or located in countries of concern. Learning from the messy Huawei and ZTE 5G unwinding, the US has been more proactive in blocking Chinese companies from international subsea cable projects involving US funding. The Federal Communications Council (FCC), which holds licensing authority for a range of ICT transactions, has also been leaning more heavily into national security issues. In new rulemaking by the FCC last year, licensees would need to disclose foreign ownership and use of “untrusted” equipment and “foreign-owned managed network service providers” and may be subject to regular national security reviews.
But the Commerce ICTS program, revived last week, may be the most potent tool for ICT-related theories of harm.
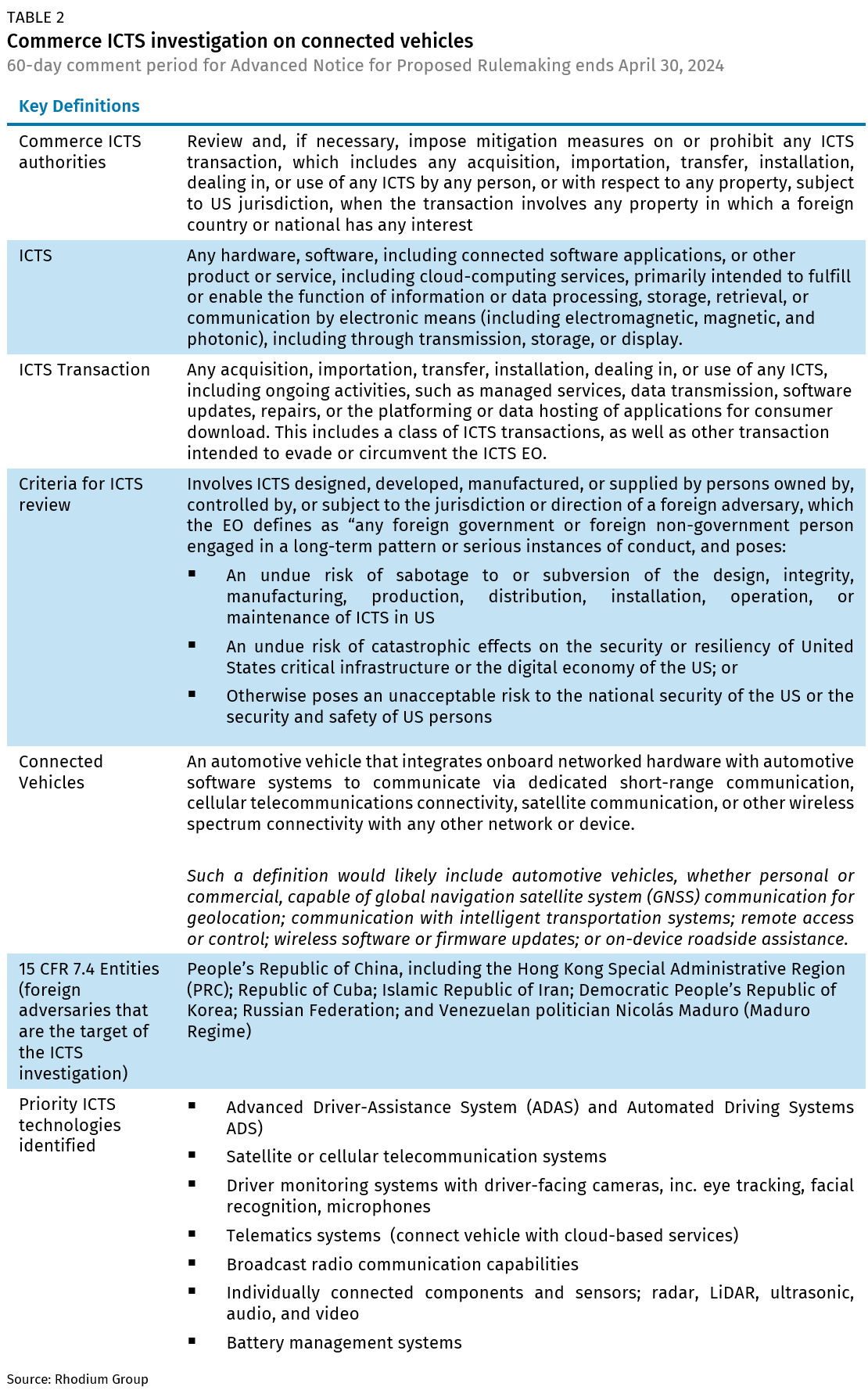
Last week’s second major policy announcement, a Commerce ICTS investigation into connected vehicles, is designed to evaluate risks to US national security stemming from ICT inputs for connected vehicles that are designed, developed, manufactured, or supplied by countries of concern.
Under a rule born during the Trump administration and expanded under the Biden administration, the ICTS rule gives Commerce and the executive branch broad authorities to review, prohibit, or impose mitigation measures on virtually any ICT transaction due to national security concerns (see Table 2 for a reference on ICTS authorities and definitions). This is an untested tool, and so the ultimate outcome of the investigation is unknown and potentially quite broad.
This investigation keeps with the Sullivan doctrine of imposing preemptive measures on technology domains. Rather than chase specific companies in complex value chains, the US is identifying entire classes of technologies—advanced semiconductors in the case of BIS export controls and connected vehicles in the case of the current ICTS investigation—around countries of concern operating and supplying key nodes in US critical infrastructure. The primary intent is to get ahead of the problem to avoid the need for costly rip-and-replace orders.
This means companies will need to undergo a complete mindset shift: away from reactive adjustments to concrete regulations toward proactive due diligence in assessing how their products and services could pose data security, cybersecurity, and ultimately national security risk to US critical infrastructure, and what measures they can take to mitigate those risks (to include foregoing Chinese partners and suppliers.)
The Commerce ANPRM deliberately defines “connected vehicles” broadly, encompassing any vehicle with even basic GPS functions (See Table 2 on key definitions of the Commerce ICTS investigation). The idea is to cast a wide net on the full vehicle ICT architecture and make it incumbent on industry players to pressure test the US administration’s theories of harm and propose reasonable mitigation measures.
The ANPRM lays out the following logic:
The argument itself is relatively simple, but the devil will be in the details in assessing to what degree individual and networked hardware and software inputs create cyber-enabled vulnerabilities. As the ANPRM argues, even if an individual component or system has a benign and highly specific function for the safety and operationality of the vehicle, such devices or software may create an entry point for a state-backed cyber actor to infiltrate the US transportation system at large.
The concern is not merely theoretical. A recent CISA/NSA/FBI report documented how China-backed hacking group Volt Typhoon has been exploiting vulnerabilities in routers, firewalls, and VPNs to target water, transportation, energy, and communications systems across the US. The report details how a malicious actor can move laterally across systems once they gain entry, putting the broader network at risk, and suggests that such operations pre-position malicious cyber actors to conduct destabilizing attacks on US critical infrastructure in a geopolitical conflict scenario. These concerns are a big driver behind another recent Executive Order and $20 billion investment through grants focused on replacing Chinese-made port crane infrastructure.
The ANPRM puts cybersecurity experts in high demand to assess these risks and offer mitigation steps. And, as many would argue, there is no way to achieve complete protection from cyberattacks; the emphasis instead should be on layered defense. Moreover, it doesn’t necessarily take a Chinese-made input to enable a PRC-backed cyber-attack. But the organizing principle at play is “an ounce of prevention is worth a pound of cure.” In operating under the assumption that foreign adversaries will continue launching cyber operations on US critical infrastructure, the US administration is looking to US industry to assist in shoring up defenses.
The ANPRM gets stretchy when it delves into why scrutiny is focused on China-linked ICT inputs. The document asserts that:
It then notes:
“According to open-source reporting, over 200 automakers that operate in the PRC are legally obligated to transmit real-time vehicle data, including geolocation information, to government monitoring centers. […] This pervasive data sharing, which provides the PRC government with detailed information on the behaviors and habits of individuals, is indicative of a broader approach to co-opting private companies—one that raises significant concerns about how the PRC government might exploit the growing presence of PRC OEMs and manufacturers of ICTS integral to [connected vehicles] in foreign markets.”
This line deserves some unpacking. As the data security EO and ANPRM outline, geolocation data can be used to track behaviors and patterns of individuals to exploit them. The US is referencing the same theory of harm here in highlighting the risk to individuals. But the use case they cite is in China, not the US. In fact, the theory of harm around a vehicle’s ability to collect personal data (including geolocation data) is the same the Chinese government has used in demanding oversight of OEMs collecting such data on persons in China.
The argument raises a host of questions on the implicit intent of potential restrictions on Chinese ICTS for connected vehicles:
It will take time for Commerce to understand the value chain for connected vehicle systems and identify chokepoints and emerging dependencies where Chinese firms are concentrated. MNCs in the connected vehicle value chain will meanwhile be operating in a cloud of uncertainty as Commerce deliberates potential measures.
That may be the point. Similar to the lengthy launch of an outbound investment screening regime, companies in this connected vehicle technology space have been put on notice. That chilling effect could deter US companies from investing in and deepening partnerships with fast-growing Chinese EV suppliers when the risk of regulatory entanglements is clearly rising.
The ANPRM language also reveals an intent to assess spillover effects of removing Chinese ICT suppliers and to identify non-Chinese suppliers to replace them. The implication is that market opportunities can expand for companies that can position themselves as compliant and China-free suppliers for the US and partner markets. This is where industrial policy incentives, trade defense, cybersecurity, and data security intertwine. For example, the ANPRM asks what ICTS hardware or software for connected vehicles Chinese entities “maintain a technological advantage over US and other foreign counterparts [in] and how may this dynamic evolve in the coming years?”
Even as economic security measures threaten to raise input costs, industrial policy incentives (like IRA tax credits that are designed to extricate Chinese inputs) combined with trade defense (like higher tariffs on Chinese-made EVs) aim to level the playing field and boost US competitiveness in markets where Chinese firms are being denied access. Industry groups like the Alliance for American Manufacturing are already explicitly advocating for “exclusionary” tariffs to fend off Chinese EV competition. Amid long-running trade disputes, ICT cybersecurity restrictions could be the more efficient means of barring Chinese EVs from the US market.
With incisive new data security measures and the potential for wide-ranging controls on connected vehicle technologies, the US has once again expanded the frontier for tech controls. Here is what we’re watching in the months ahead:
Note
US policymakers are wagering that industry and partners will align with US controls and that time and innovation are on Washington's side.
Note
The proposed approach targets a smaller set of technology categories, but uncertainties in the regulatory draft language raise questions about its ultimate scope.
Note
A deep look at where Chinese chipmakers and their state backers are likely to focus their resources after the export controls imposed by the US on October 7, 2022
Note
The Biden administration's new technology controls aimed at China will have far-reaching consequences. We assess the policy objectives behind them, the impact on the semiconductor industry and how China and US allies may respond.